Sponsored Content: Recently IT Security experts from Singapore and Philippines joined BlackBerry and Focus Networks to discuss security and privacy.
Security and privacy are two different concepts that often can be associated with each other, but it is entirely possible for organisations to secure themselves, but still not be private. How does this happen?
Privacy refers to the right to have control over how your information is collected, shared, and used. Security generally refers to the protection of data and the standards that organisations plan to put around it.
There has been long-standing tension between protecting data and the privacy surrounding the data collected, shared, and used. That has been even more apparent in the current digital age for industries like banking, financial services, and insurance (BFSI).
Recently Focus Network, in partnership with BlackBerry, joined by 20 CIOs, and leading IT Security experts from Singapore and Philippines, to discuss the vulnerabilities in these industry trends and how having a balance of both privacy and security maturity can help de-risk an organisation’s digital strategy.
Top priorities in the BFSI sector in 2020 primarily focuses on technology trends that will disrupt both financial institutions, traditional business model and workforce.
During this virtual roundtable, the following key topics were discussed:
- Fintech taking over as the new business model
- Public cloud becoming more a dominant infrastructure in BFSI
- The increased dependency of “customer intelligence” and information
- Mobile workforce
If organisations think of a scenario where they have gone to great lengths to secure personally identifiable information (PII). The data is encrypted, access is restricted, and multiple overlapping monitoring systems are in place. However, if that PII was collected without proper consent, you could be violating a data privacy regulation even though the data is secure.
It is also possible for privacy to be ignored even when there is consent — for instance, let usdiscuss the security and privacy of anti-virus software.
Security can protect FIs from malicious files and programmes, which help to scan computers from threats and vulnerabilities. Paid options normally give even more security features like web plugins which keep you off malicious sites, password managers, ad blocking software etc.
During the roundtable, Amanda Chan ASEAN enterprise account lead at BlackBerry said it is natural to think security has dramatically improved based on this software, but then we cannot assume privacy has been achieved.
“You are putting your trust in these third-party companies to scan the contents of every file you download onto the computer, every programme you open,” she stated. “And a lot of these information are sent to anti-virus companies to help them improve their service and detection. We do not really know what they are doing with this data, they very well can be using this information and selling them off to a third party for unauthorised usage.”
Chan notes in September 2017 the US Government banned federal agencies from using Kaspersky Labs software. This is due to “allegations” about co-operation between Kaspersky and Russian intelligence agencies.
“Shortly after, the FBI began pressuring retailers in the private sector to stop selling Kaspersky products, and the UK government issued a warning to government departments about the security risks of using Kaspersky software,” she said.
“This is why it can’t just be assumed that there is privacy just because security measures and controls are in place, we now need to further relook into some events.”
Another example relates to the financial sector on how information is collected during events, roadshows, or sign-ups.
“Be it an insurance agent or personal banker or wealth manager, he or she might have a client signed up with the bank or insurance company via what the organisation perceives as a secure application or secure device,” said Chan.
“A ticked checkbox however for user consent cannot imply that privacy has been respected. It simply implies that a user has allowed the organisation to collect his or her personal details for a single sole purpose- such as newsletters or advertisements. Should these details, for example, be copied to an unsanctioned repository due to poor app security framework and controls, privacy potentially can be compromised.”
Repercussions and risks of accepting this assumption.
The original point of reference for these tech influencers was taken from a PWC paper that discussed BFSI technology trends for 2020 and beyond.
Traditionally most of BFSI SaaS Based applications in the cloud are considered non-core/non-critical applications.
- However, the change we see today, shows more and more BFSI clients looking to move core applications into the cloud.
- We can consider SaaS based applications in two ways- one workforce related (such as highly sensitive HR, board members or finance type of applications) and two, being client services related (for instance middle and front office core banking applications that directly impacts a client’s banking process.)
It is important to note that SaaS based applications are not securely coded the same. A simple example would be some SaaS based apps rely on the device OS encryption and others don’t. Others might be using substandard or less secure version of AES encryption. It’s very common for a user to have corporate applications running on multiple device or OS with varying security framework.
- An untested or non-comprehensive security model should be a concern for customers in regulated industries and all other security-conscious IT environments.
- How will banks achieve a consistent way of building secured applications regardless if they are native or hybrid apps, agnostic to device and OS etc.
The question then becomes how to mitigate that. There are many angles to approach this challenge but the risk mitigation for this discussion refers entirely to BlackBerry’s security fundamentals.
Solutions like BlackBerry Unified endpoint management (UEM) platform provides services to developers and infra professionals such as:
1.) Application containerisation
2.) Secured APIs
3.) Secure coding for most frameworks (both native and cross development)
4.) Cross-platform security and shared services
These libs of framework and services are provided in the form of SDK.
THE UEM Platform itself is built agnostic to any OS, devices, or application framework. The platform on its own has 80+ certifications, with some key mentioned such as FIPS140-2 and Common Criteria EAL4+.
What this means is all applications that have been incorporated with our SDK sitting on the platform will be consistently secured regardless if they are in the cloud or on-prem. Data at rest, in transit are secured with the same standards regardless if it’s a Microsoft app, SaaS based app or in house app.
The roundtable also looked at how fintechs are slowly becoming the new business model. What exactly does that mean?
- Basically, it just illustrates how omnichannel and frictionless client services are becoming the new normal.
- Some examples are open banking/peer to peer transactions, digital or remote advisoryApps (via video conferencing/ mobile chatbots) and even digital or automated account opening.
- This brings about a distinct concern on privacy. How are financial institutions able to ensure the user’s identity is not compromised when accessing these applications or engaging in frictionless client services? How can they ensure there is privacy in all transactions and identity is non-repudiated?
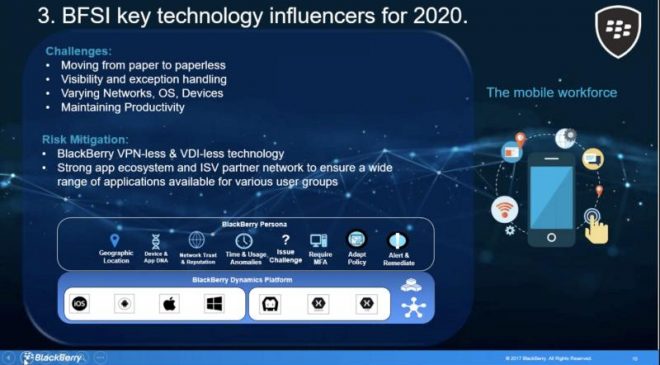
According to Chan, the BlackBerry Persona- is another feature layered on the UEM platform. BlackBerry Persona basically uses an AI risk scoring engine developed based on the zero-trust principle.
- Trust can no longer be assumed just based on a password or two-factor control.
- Trust should be earned at every point in a service request.
- From when a person keys in his or her password to the point they are granted access into a network or a file share or databased, all the way until they have successfully exited the transaction and session.
- continuous authentication during a service request is only feasible by using behaviour. (As it needs to be done on the back end rather than for a user to address a challenge every few seconds.)
- In other words, a person’s behaviour becomes their new password or the new source of truth.
- How then can a person’s behaviour be measured?
- So here on the slide, the diagram shows a summary of the perimeters (in broad categories) in which persona uses to conclude a risk scoring for a person.
- App and device DNA, geo-location, network trust and reputation, time and usage anomalies (can explain briefly on device and app DNA)
- Because Persona technology is layered on top of UEM, all device or application that is on UEM can have access to person capabilities as well. (it’s available for both on-prem and cloud applications)
- Users should not feel hindered and security should not be compromised.
The mobile workforce.
Just like Cloud, mobility is a technology influence. It has become prevalent and more widespread in recent years.
Some of the distinct challenges really is about ensuring effective digital adoption, gaining visibility and control despite having multiple networks, OS and devices in play.
How can an organisation achieve this? How is it possible to have adoption and productivity while ensuring privacy and security?
- Proportionate risk mitigation where users can have their security policies and challenges dynamically adjusted based on a real-time risk scoring.
- Again, this concept of zero trust can be applied in the mobile workforce.
BlackBerry digital work-spaces basically allow companies to use both UEM and BlackBerry persona for the mobile workforce.
- It provides web portal and mobile workspace for secure online and offline access to corporate on-premises or cloud content, including Microsoft Office 365 resources ISV apps and custom applications.
- The system relies on multifactor authentication, analytics, encryption, and file system-level permissions and includes dynamic enforcement of access rules – not only for a user’s identity but also for their device and the context in which they’re attempting access. The result is that users are given the minimum amount of access to accomplish a specific task.
- The last key influence we are going to discuss will be on customer intelligence and analytics. Learning about specific client habits through customer intelligence and analytics not only allows an organisation to have real-time decision making but also improves overall customer satisfaction. This however inherently poses a huge privacy concern.
- How can organisations vouch that Data being collected for a certain marketing use is created, ingested, and destroyed appropriately? Is data being created in a secure manner (i.e. on paper forms or insecure application/landing pages? Created in house of by 3rd party vendors?)
- BlackBerry’s SDK provides Secure APIs and extensive Frameworks and secure routing. Hence this allow developers to integrate security and granular controls within applications (regardless in-house or third party). This gives the middleman or employees no choice but to collect data in a standardised and secure way. For example, forcing all employees to adopt data collection on application and disallowing application screen shots, copy-paste or backup to unsanctioned repositories. User groups can be created to allow app level granularity in controls and policy.
It is imperative for organisations to filter both key business activities and internal workforce demands through a privacy and security type of lenses.




